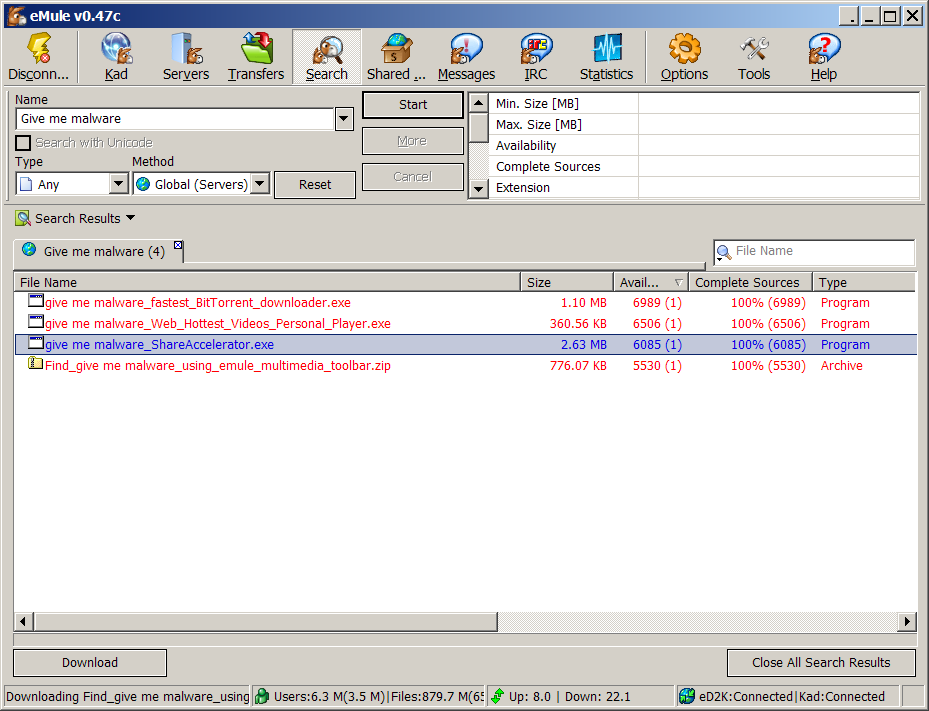
Apparently, rogue servers listening on the p2p Kad network intercept the search terms of queries and generate on the fly appropriate file names linking to files that contain malware.
For a example, a random search term, like "give me malware", will return the following file names.
give me malware_fastest_BitTorrent_downloader.exe give me malware_Web_Hottest_Videos_Personal_Player.exe give me malware_ShareAccelerator.exe give me malware_using_emule_multimedia_toolbar.zipAs the image below demonstrates, the availability of these files is also doctored to look artificially high. (Yes, I know that one shouldn't use unknown servers.)
Two virus scanners didn't find anything suspicious in the files. Specifically, I run Clamwin and Vasilis Prevelakis Symantec antivirus without obtaining any warnings. However, Panagiotis Louridas running Avira AntiVir suceeded in identifying two of the four malware programs:
viri/give me malware_ShareAccelerator.exe [DETECTION] Is the Trojan horse TR/Drop.HotWebBar.C viri/give me malware_Web_Hottest_Videos_Personal_Player.exe [DETECTION] Contains signature of the dropper DR/WhenU.A.9According to Avira, the two malware programs were added to the definition file on February 5th, 2007.
Moral: malware writers are getting increasingly sophisticated; antivirus programs are trailing behind.
Comments Post Toot! TweetUnix make vs Apache Airflow (2024-10-15)
How (and how not) to present related work (2024-08-05)
An exception handling revelation (2024-02-05)
Extending the life of TomTom wearables (2023-09-01)
How AGI can conquer the world and what to do about it (2023-04-13)
Twitter's overrated dissemination capacity (2023-04-02)
The hypocritical call to pause giant AI (2023-03-30)
AI deforests the knowledge’s ecosystem (2023-03-16)
How I fixed git-grep macOS UTF-8 support (2022-10-12)
Last modified: Friday, February 16, 2007 12:40 am
Unless otherwise expressly stated, all original material on this page created by Diomidis Spinellis is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License.