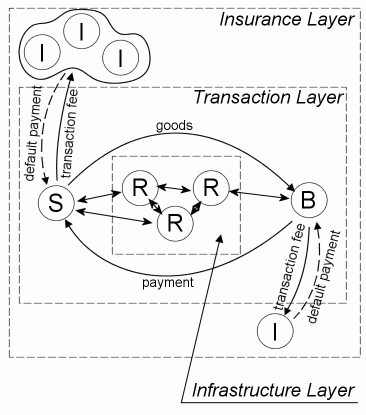
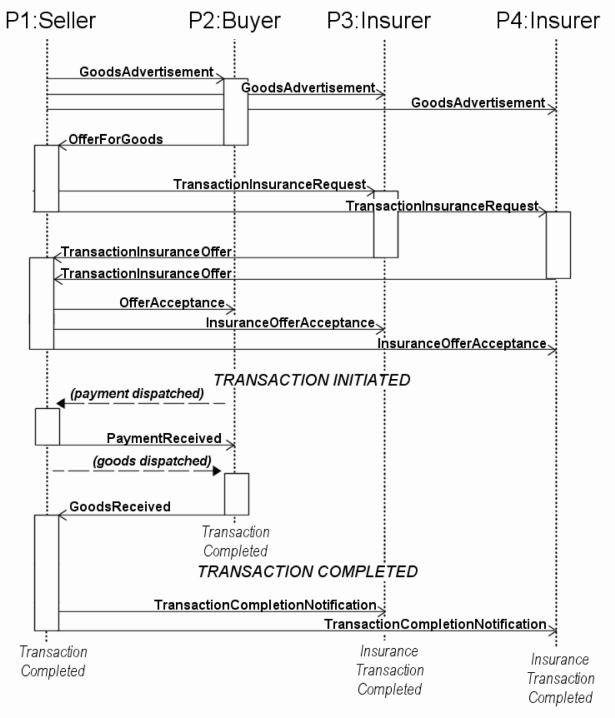
This is an HTML rendering of a working paper draft that led to a publication. The publication should always be cited in preference to this draft using the following reference:
- Stephanos
Androutsellis-Theotokis and Diomidis Spinellis.
Ptrim:
A market-based approach to managing the risk of peer-to-peer
transactions.
In Sonia Bergamaschi, Zoran Despotovic,
Sam Joseph, and Gianluca Moro, editors,
DBISP2P 2007: Fifth International Workshop on Databases, Information
Systems and Peer-to-Peer Computing, September 2007.